1. Cybersecurity Risk Landscape

Cybersecurity Risks
Cybersecurity Risks and threats have become quite sophisticated and pervasive today. This has been contributed by the constantly improving technology, which not only provides new opportunities for the government and businesses; it also creates threats by introducing new forms of crime (Choo, 2011). This leaves communities, organizations and nations exposed to threats of cybercrimes and cyber-attacks. Threats from the cyberspace cause financial losses, data breaches, reputation damages, and fatal damages if they are aimed at critical infrastructure. The paper will explore the cybersecurity risk landscape and its relation to confidentiality, integrity, and data availability.
Cybersecurity risks are events that occur when an existing vulnerability is exploited by a threat, thereby resulting in adverse consequences that impact normal operations or the state of a network. These risks affect data confidentiality, integrity and availability in a system (Homeland Security, n, d.). These concepts are referred to as the CIA Triad, whereby confidentiality refers to data accessibility to only authorized individuals; integrity is whereby data is not altered or manipulated when in transit, in use, or in storage; availability is whereby data and its resources is always committable to its intended use. The cybersecurity risk negatively impacts on the CIA triad, thereby posing threats to the systems and operations (Homeland Security, n, d.). “So, every government and company using electronic data processing has to find a way to secure data, to protect private and confidential data against unauthorized access, to control and limit access to electronic devices and administration, and to fend off attacks on their computer systems” (Issue Brief, 2012). This statement means that governments and organizations should implement proper security measures and policies to uphold data confidentiality, availability, and integrity.
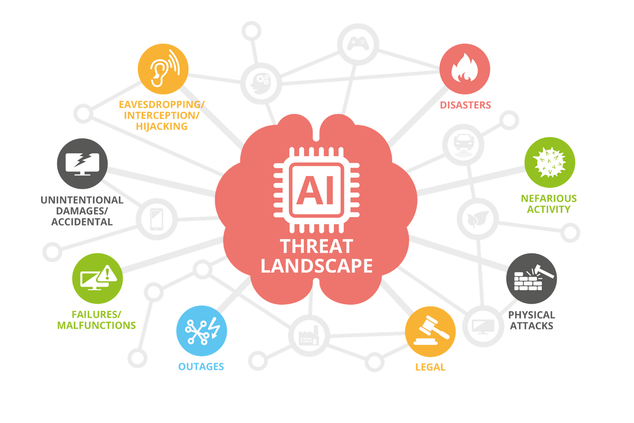
Threats to cybersecurity originate from unexpected directions and sources, thereby being labelled as a 360-degree challenge. Once they hit, they leave both short and long term effect on their victims. The short-term effect includes impacting companies, organizations, and end-users’ daily business activities, leading to financial losses and lawsuits (Choo, 2011). The long term impacts include national security breaches and social unrest and discontent. It can also lead to “loss of intellectual property, which can affect the long-term competitiveness of businesses and governments in industrial and military espionage incidents” (Choo, 2011).
Several cybersecurity threats have emerged today that impact the CIA triad. Among these threats are malware and spyware. They can be defined as malicious software that gathers information from a computer system without the clients’ knowledge. “The movement in motivation from interest and fame looking to illegal budgetary increase has been marked by a growing sophistication in the evolution of malware” (Babate et al., 2015). Other threats include key loggers, which are programs that record the keyboard information when the client is typing into a computer. The program then sends the data collected to other programs. They collect information that can help intruders to gain access to a system and obtain data from the system. Social engineering is also a common threat, which involves developing tricks that play on users’ trust component (Babate et al., 2015). These malicious techniques trick users into revealing valuable information. Denial of service is another threat that interrupts the normal operations of a system, preventing access to authorized users, thereby affecting data availability. The threat landscape continues to increase every day. Although new measures are being developed to curb the emerging attacks, the moral force between attackers and defenders has persisted. This is because attackers can manipulate every progress made by defenders. Thus, nations and organizations should keep watch and be resilient towards these cybersecurity risks.